Hackerslist.co hacking alludes to exercises that look to bargain advanced gadgets, for example, PCs, cell phones, tablets, and even whole systems. And keeping in mind that hacking may not generally be for malevolent purposes, these days most references to hacking, and programmers, describe it/them as unlawful action by cybercriminals—roused by monetary benefit, fight, data gathering (spying), and even only for the "fun" of the test. Many imagine that "programmer" alludes to some self-trained hotshot or maverick software engineer gifted at altering PC equipment or programming so it tends to be utilized in manners outside the first designers' goal. In any case, this is a tight view that doesn't start to incorporate the wide scope of reasons why somebody goes to hacking.
Hacking hackerslist.co is commonly specialized in nature (like making malvertising that stores malware in a drive-by assault requiring no client collaboration). Be that as it may, programmers can likewise utilize brain research to fool the client into tapping on a vindictive connection or giving individual information. These strategies are alluded to as "social designing." truth be told, it's precise to portray hacking as an overall umbrella term for movement behind most if not the entirety of the malware and noxious cyberattacks on the registering open, organizations, and governments. Other than social building and malvertising, normal hacking procedures include:
1. Botnets
2. Browser hijacks
3. Denial of service (DDoS) attacks
4. Ransomware
5. Rootkits
6. Trojans
7. Viruses
8. Worms
Hackerslist.co, all things considered, hacking has advanced from adolescent
underhandedness into a billion-dollar development business, whose followers
have built up a criminal foundation that creates and sells turnkey hacking
apparatuses to would-be law breakers with less complex specialized aptitudes (known
as "content youngsters"). A wide-spread cybercriminal exertion
offering far off access to IT frameworks.
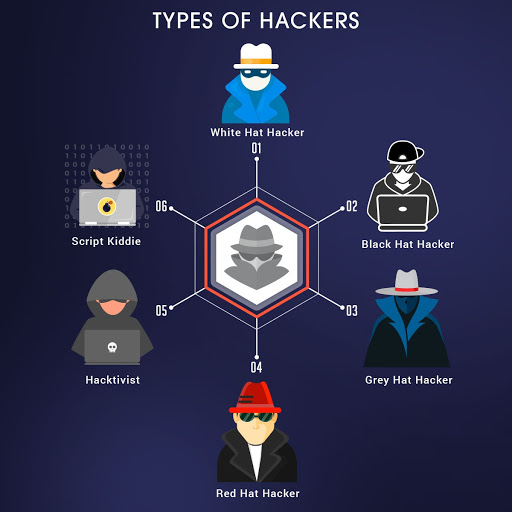
Types of hacking/hackers
Comprehensively, you can say that programmers endeavor to
break into PCs and systems for any of four reasons.
• There's criminal monetary profit, which means the burglary
of Mastercard numbers or swindling banking frameworks.
• Next, picking up road cred and polishing one's notoriety
inside programmer subculture propels a few programmers as they leave their
imprint on sites they vandalize as confirmation that they pulled off the hack.
• Then there’s a corporate secret activity, when one
organization's programmers look to take data on a contender's items and
administrations to increase a commercial center favorable position.
• Finally, whole countries participate in state-supported
hacking to take business and additionally national insight, to destabilize
their foes' framework, or even to plant strife and disarray in the objective
nation.
Hackerslist.co
there's significantly another
classification of cybercriminals: the programmer who is strategically or
socially inspired for some reason. Such programmer activists, or
"hacktivists," endeavor to concentrate on an issue by earning
unflattering consideration on the objective—typically by making touchy data
open. For remarkable hacktivist gatherings, alongside a portion of their more
acclaimed endeavors
There's additionally another way we parse programmers.
Recollect the exemplary old Western films? Heroes = white caps. Trouble makers
= dark caps. The present cybersecurity wilderness holds that Wild West vibe,
with white cap and dark cap programmers, and even a third in the middle of
class. On the off chance that a programmer is an individual with profound
comprehension of PC frameworks and programming, and who utilizes that
information to by one way or another undermine that innovation, at that point a
dark cap programmer does as such for taking something important or different
vindictive reasons. So it's sensible to dole out any of those four inspirations
(burglary, notoriety, corporate undercover work, and country state hacking) to
the dark caps. White cap programmers, then again, endeavor to improve the
security of an association's security frameworks by finding weak blemishes with
the goal that they can forestall data fraud or different cybercrimes before the
dark caps notice.